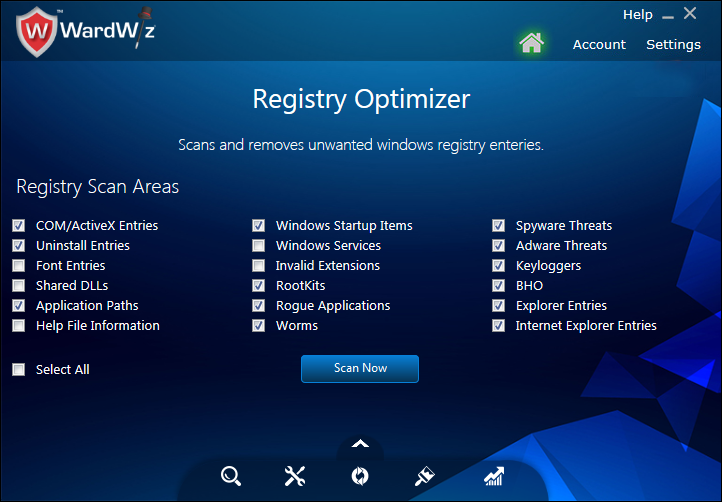
|
Type of Entry
|
Description
|
Malicious Activity
|
|
COM/ActiveXEntries
|
These are small programs inserted in web pages to improve the functionality of web pages, as they are programs, they can be targeted by the Viruses.
|
These entries can be used to get control over your working web based applications.
|
|
Uninstall Entries
|
Sometimes, when we uninstall the software some of the entries of the software might still lie in the registry.
|
These entries slow down your computer’s performance by consuming storage space. Therefore, such entries reduces your computer system performance.
|
|
Application Paths
|
Few corrupted application paths might still be present in your registry even after uninstallation of the program.
|
These paths slow down computer system performance.
|
|
Windows Startup Items
|
Some applications load themselves automatically on start of the computer. In some cases malicious programs such as Malware, Trojan, Worms, Spyware and Virus loads in this manner.
|
These kind of applications can hijack your computer. So it is important to remove such application entries from your windows start up registry.
|
|
Rootkits
|
Rootkits are hidden malicious software programs which on activation slow down the duration of system booting process.
|
These programs slow down the speed of system booting process.
|
|
Rouge Application
|
Rough application is a software program which enters in the system through internet and forces the user to believe that the system is in danger because of virus infection.
|
On acceptance of its misleading guidelines which provokes you to install unnecessary program. The installed program may have threatening intension.
|
|
Worms
|
Worm is a standalone computer program which replicates itself from one drive to other another.
|
Spreads using the computer network and harms the computer network by consuming the internet bandwidth (Speed).
|
|
Spyware Threats
|
Hackers tries to steal your confidential information from your computer with the help of Spywares
|
Hackers can launch such kind of programs to enter in your computer system.
These programs keep watch on your activities with your computer system.
|
|
Adware Threats
|
Adware or advertising - supported software automatically displays unwanted advertisements in order to generate online revenue for its author.
|
An advertisement distracts you on the working screen, sometimes ads' popup covers the working area and leads you forcefully towards unnecessary internet pages.
|
|
Keyloggers
|
Keyloggers are designed to trace the key strokes applied by your computer Keyboard.
|
Such programs launched with the intention of stealing your passwords, account numbers, and confidential information. These software marks hidden entries in Registry.
|
|
BHO (Browser Helper Object)
|
Browser Helper Objects load automatically whenever you open the website.
|
These plugins are prone to the infection. The hacker can hack and monitor the webpages accessed by the user using these plugins.
|
|
Explorer Entries
|
The internet explorer saves the recently visited pages to speed up the opening process on next visit.
|
Internet Explorer entries must be removed to keep malicious websites away from your recent search.
|